The silent, intricate web of code that underpins our global economy and essential services has become the newest and most fertile battleground for sophisticated cyber adversaries. This report analyzes the systemic vulnerabilities emerging from the software supply chain, a foundational element of modern society that is increasingly targeted to disrupt national infrastructure. The interconnected nature of software development, once a catalyst for innovation, now presents a critical point of failure with far-reaching consequences.
The Invisible Backbone: Understanding the Modern Software Supply Chain
How Interconnected Code Powers Modern Society
Modern applications are rarely built from scratch; they are assembled from a vast ecosystem of pre-existing components. This includes open-source libraries, commercial software packages, and application programming interfaces (APIs) that connect disparate services. This modular approach accelerates development and fosters innovation, allowing organizations to deliver complex functionality rapidly.
From financial trading platforms to hospital management systems and the control systems governing power grids, nearly every facet of modern life depends on this layered software. The efficiency gained, however, comes with an implicit trade-off. Each component, sourced from a different developer or organization, introduces a layer of dependency and, consequently, a potential vector for attack. The trust placed in these external codebases is the bedrock of digital infrastructure, yet it is often unverified.
Mapping the Attack Surface from Open-Source to Cloud APIs
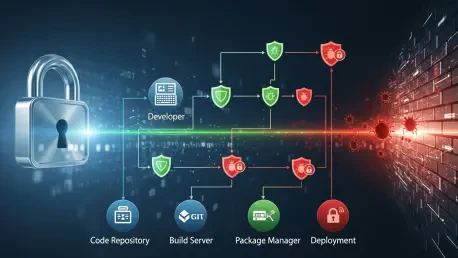
The attack surface of a modern organization is no longer confined to its own perimeter. It extends outward through every software dependency, creating a complex and often poorly understood network of risk. An attacker who compromises a single, widely used open-source library can effectively gain a foothold in thousands of downstream applications and systems simultaneously.
This expanded threat landscape also includes cloud services and their associated APIs, which have become integral to operations. A vulnerability in a cloud provider’s infrastructure or a compromised API key can expose vast amounts of sensitive data or disrupt critical services. Mapping this sprawling attack surface is a monumental challenge, as many dependencies are nested deep within other components, making comprehensive visibility difficult to achieve.
A New Frontier for Cybercrime Trends and Financial Impacts
The Upstream Shift: How Attackers Weaponize Software Dependencies
Cybercriminals have recognized the high-leverage potential of targeting the software supply chain. Rather than attacking thousands of individual organizations, they are increasingly shifting their focus “upstream” to compromise the software developers and tools that feed the entire ecosystem. By injecting malicious code into a popular software update or development tool, they can distribute malware covertly and at a massive scale.
This strategic pivot represents a significant evolution in cybercrime tactics. These attacks are stealthy, often evading traditional security measures that focus on perimeter defense. The compromised software is delivered through legitimate update channels, effectively using the vendor’s own trust and infrastructure as a delivery mechanism. This method grants attackers privileged access deep inside target networks, often going undetected for extended periods.
Quantifying the Threat: The Soaring Costs of Supply Chain Breaches
The financial and operational repercussions of these attacks are staggering. Industry analysis from 2025 revealed that breaches originating from third-party software had doubled, accounting for 30% of all data breaches. The average cost of such an incident climbed to $4.4 million, not including the immense reputational damage and loss of customer trust.
These figures underscore a growing consensus: securing the digital supply line is one of the most vital cybersecurity challenges of the current decade. The costs are not merely financial; a successful attack on critical infrastructure could lead to power outages, disruptions in healthcare services, or instability in financial markets, highlighting the profound societal impact of these digital threats.