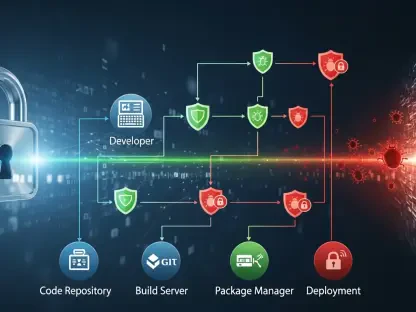
In recent years, the cybersecurity landscape has become increasingly complex and treacherous, posing significant risks to modern software development. High-profile cyberattacks have demonstrated the vulnerabilities of even the most robust applications, making security a critical component of a developer’s skill set. The magnitude of threats faced by companies today underscores the pressing need for secure coding practices that protect both users and organizational assets. This article outlines a comprehensive approach for integrating effective security measures into every phase of the software development life cycle. By following these ten essential steps, developers can better defend their creations against adversaries, thus safeguarding vital data and intellectual property.
1. Begin with the Essentials
The foundation of secure software development is an understanding of known vulnerabilities. By mastering existing weaknesses, developers can more effectively defend against sophisticated zero-day exploits. Essential resources like OWASP (Open Worldwide Application Security Project), MITRE, and NIST NVD (National Institute of Standards and Technology’s National Vulnerability Database) provide the necessary frameworks and guidelines for identifying critical security risks within various applications, including web, mobile, API, and smart contracts. These resources are invaluable for anyone in the development field, as they offer insights into common threats and provide strategies to mitigate them effectively. Training developers to regularly consult and apply learnings from these resources can serve as a vital first line of defense against potential security breaches.
In addition to understanding existing vulnerabilities, staying updated on emerging threats is crucial. Cyber threats constantly evolve, requiring developers to be proactive in their efforts to stay informed. This can involve participating in security conferences, subscribing to relevant security-focused publications, or being part of developer forums concentrating on security best practices. By maintaining an awareness of the shifting risk landscape, developers can ensure they are always ready to address both longstanding and new security challenges head-on. Ensuring a solid grounding in these essentials empowers developers to create safer and more resilient software applications.
2. Establish Secure Coding Practices
Standardizing secure coding practices across teams is crucial for mitigating software vulnerabilities. This requires a cultural shift within development teams where secure coding becomes the default rather than an afterthought. Two critical practices are input validation and input sanitization. Input validation involves ensuring that incoming data is appropriate and safe for its intended use. It minimizes the risk of logic errors and potential downstream failures that could be exploited by malicious entities. Ensuring robust validation of all input data is not merely a safeguard; it is a proactive measure that protects an application from a wide array of vulnerabilities introduced through malicious input.
Input sanitization, on the other hand, involves removing or neutralizing potentially harmful content. This is essential in preventing exploits like cross-site scripting (XSS) and SQL injection attacks, which can compromise application integrity. By sanitizing input, developers can effectively neutralize harmful scripts before they interact with sensitive system components, maintaining the application’s security. Fostering a development environment that prioritizes these practices will result in more robust applications and cultivate a security-first mindset among team members. Training and real-world application are key. Regular code reviews and collaborative discussions on potential vulnerabilities can facilitate this cultural shift toward routine security practices.
3. Perfect Access Management
Access management plays a pivotal role in safeguarding sensitive resources within software applications. Moving beyond basic security measures, developers should adopt a least-privilege approach. This principle dictates that users and systems are granted only the permissions necessary to perform their required tasks, thus reducing the risk of unauthorized access. Implementing least-privilege requires a thorough assessment of each user’s roles and responsibilities to ensure they retain only the permissions essential for their work. This approach not only minimizes exposure in the event of a security breach but also enforces a more controlled environment where accountability is heightened, and rogue actions are more easily detectable.
The next step is the implementation of strong authentication and authorization protocols, which are crucial in defining who can access what and under what circumstances. Well-defined access controls ensure that only authorized users can interact with specific components, which is indispensable for maintaining the confidentiality and integrity of an application. Combining this with multi-factor authentication (MFA) can add an additional layer of security, ensuring that even if credentials are compromised, unauthorized access is thwarted. A comprehensive access management strategy that includes routinely reviewing and auditing existing permissions and access paths can greatly reduce vulnerabilities and foster a secure environment throughout the software’s lifecycle.
4. Pay Attention to APIs
APIs are the backbone of modern applications, serving as the conduits for data exchange between systems. Despite their integral role, APIs often present significant security risks, with vulnerabilities like broken authentication and authorization posing major threats. These vulnerabilities have increased dramatically in recent times, emphasizing the importance of designing API security from inception. Baking in security measures from the start rather than retrofitting them later is essential in creating APIs that stand strong against adversaries. API security design must account for safe data handling, thorough input validation, and strict authentication controls to effectively protect against unauthorized access and data breaches.
APIs should be viewed not just as technical interfaces but as potential attack vectors. This mindset encourages the implementation of robust security measures, such as rate limiting and input validation, to help mitigate abuse. Moreover, secure APIs require stringent access controls to ensure that only authenticated and authorized entities can make requests. Comprehensive documentation and ongoing monitoring of API usage can further aid in detecting and responding to security incidents promptly. Developers should prioritize creating secure and defensible APIs to maintain the reliability and confidentiality of the services they provide. This proactive approach will ensure that inadvertent exposures or vulnerabilities are kept to a minimum.
5. Presume Data Sensitivity
Developers must treat all data as though it is constantly under threat. Protecting sensitive information requires a comprehensive strategy that involves encryption both at rest and during transmission. Encryption ensures that even if data is intercepted, it remains undecipherable to unauthorized parties. Developers should leverage strong, up-to-date encryption algorithms to prevent potential breaches. Encrypting data that includes personally identifiable information (PII), payment details, internal identifiers, and other sensitive types is crucial for maintaining trust and legal compliance. Questions regarding the necessity and security of data during processes such as logging, auto-completion, and transmission should be addressed proactively.
Beyond encryption, developers need to critically evaluate the data they are dealing with, questioning its necessity and the potential risks of exposure. Minimizing data collection and retention can significantly reduce an application’s risk profile, curtailing the scope of potential attacks. Regular audits can help ensure compliance with data protection best practices, adapting strategies as new threats and technologies emerge. Creating a security-conscious environment that prioritizes the integrity and confidentiality of data from the outset will mitigate risks and preserve user trust. Developers must act as vigilant guardians of data, understanding that protective measures are essential and ever-evolving.
6. Document and Track Application Activity
Detailed application logging and monitoring are essential for security and compliance purposes, aiding in threat detection and incident response. Comprehensive logging ensures transparency in tracking user activities, helping to identify potential red flags and abnormal behavior indicative of a security breach. Thorough documentation of key user activities and application transactions can serve as an effective early-warning system, enabling teams to detect and address issues before they escalate. Properly implemented logging will also ensure compliance with regulatory requirements by providing an auditable trail of relevant events and activities related to the application’s operation.
Logging systems should include detailed information on user context to accurately identify suspicious activities and employ effective encoding to guard recorded data against injection attacks. In addition to logging user interactions, continuous monitoring of the entire software development life cycle is essential to maintaining robust security postures. Adopting real-time alerting systems provides timely notifications of potential threats, facilitating prompt incident response and reducing damaging consequences. Comprehensive monitoring should encompass all phases of development and include design, coding, integration, and deployment to ensure a proactive security regime.
Equally important is implementing strategies for efficient threat detection and response. Establishing and maintaining clear incident response plans ensures that teams are equipped and ready to act against security incidents. This preparedness includes defining teams responsible for handling incidents, creating effective communication channels for prompt sharing of critical information, and maintaining reliable recovery procedures to restore services securely and swiftly. Constant vigilance, through proactive monitoring and comprehensive logging, is vital in maintaining a robust line of defense that stays aligned with evolving vulnerabilities. Secure applications necessitate a culture of security vigilance.
7. Embed Security Throughout Development
A commitment to security must permeate every stage of the software development life cycle, from initial planning and architectural design phases through to deployment, testing, and ongoing maintenance. When security measures are integrated into each phase, potential vulnerabilities can be identified and addressed early on, reducing the risk of issues arising later in the process. Developers must be trained to adopt a security-first mindset, thinking like defenders as they develop software. This proactive approach ensures that potential security flaws are discovered and resolved during the development process, rather than being left to become costly problems in the future.
A critical component of embedding security throughout development involves fostering a culture that prioritizes security from the ground up. Encouraging developers to consider security implications when designing and implementing features ensures they build resilient systems that can withstand attacks. This often requires collaboration between developers, quality assurance teams, and security experts to identify potential risks and develop adequate defense mechanisms. By promoting cross-functional communication and encouraging developers to share their security knowledge and experiences, teams can collectively work toward creating more secure and resilient software systems.
To ensure the continued focus on security, organizations should invest in ongoing training programs that foster a deep understanding of both traditional security principles and current threat trends. This can include workshops, online courses, or interactive training resources tailored to various roles within the development team. Prolonged dedication to security competency cultivates agile workflows conducive to faster, more robust software releases. This continuous investment in skills development improves the organization’s resilience to evolving threats and enhances the overall security posture of its software products.
8. Build on a Secure Foundation
A secure software development process necessitates a robust and well-rounded foundation that extends across the entire software life cycle. Comprehensive security strategies must address every aspect of the software development pipeline, from development environments to integration and deployment. This includes ensuring that each tool, library, API, and cloud service used in the software development process is properly secured and up-to-date. As modern applications become increasingly modular, it’s vital to safeguard each component, such as APIs, cloud servers, containers, and microservices, which can provide potential entry points for attackers.
The complexities of contemporary software ecosystems demand that stakeholders remain vigilant throughout the entire software life cycle. One notable challenge is that attackers frequently attempt to compromise software before it even reaches production. As such, it is important to have a strategy that emphasizes visibility and control across the entire development environment, proactively identifying and addressing potential risks in their early stages. Monitoring and securing these environments can prevent potential breaches and maintain the software’s integrity from the outset. Developing this kind of comprehensive strategy helps eliminate vulnerabilities before they can be exploited.
Ongoing security audit initiatives, periodic code reviews, and user training should be paramount to reduce the risk of application exposure. A solid foundation is fundamental to creating resilient applications that perform effectively in the face of ever-evolving cybersecurity threats. By consistently prioritizing and investing in security from the ground up, development organizations can protect their software products, safeguard user data, and ensure compliance with industry regulations. Ultimately, embedding a strong security foundation into development environments and processes ensures that the resulting software is both robust and effective, providing confidence to stakeholders and end-users alike.
9. Mitigate External Risks
In the contemporary digital ecosystem, software applications are built upon an intricate network of third-party libraries, frameworks, cloud services, and open-source components. While these add-ons streamline development, they also introduce potential vulnerabilities that attackers can exploit. To effectively mitigate external risks, development teams must prioritize the management of third-party components with comprehensive assessment and continuous monitoring. An effective strategy begins with validating the software, particularly third-party libraries, which entails thoroughly examining the software for any known vulnerabilities and ensuring that only secure and trusted resources are integrated into systems.
Utilizing tools and platforms that provide ongoing monitoring and threat detection for third-party components is essential for identifying and addressing potential problems before they escalate. Implementing an automated software supply chain security solution can provide continuous insights into vulnerabilities that could put the software at risk and remedy gaps before they manifest as exploits. This approach includes regularly updating these components to the latest versions and applying appropriate patches to guard against known security issues. Moreover, working towards a holistic understanding that each dependency brings potential exposure will inspire teams to find creative ways to reinforce weak spots and bolster the overall security of the software ecosystem throughout its development.
10. Commit to Continuous Monitoring
An essential aspect of maintaining robust software security in the face of ever-evolving threats involves committing to a program of continuous monitoring and improvement that adapts to changes in the threat landscape and the development process. This ongoing process should encompass regular reviews and updates of secure development practices to ensure that all security measures are up-to-date and effective. Conducting regular audits and vulnerability assessments further helps in maintaining the security and integrity of the developed applications, fostering a safety-first approach at every stage of development.
A continuous improvement program also involves investing in comprehensive role-specific training to ensure all team members remain proficient and informed about the latest security threats and best practices. Collaborating with security experts and keeping communication channels open within development teams helps identify potential areas for enhancement and improve the organization’s overall security posture. To remain proactive in the face of dynamic security challenges, teams are encouraged to develop standardized response and recovery plans to address incidents swiftly and minimize potential damage.
Finally, staying vigilant about the evolving threat landscape and emerging trends in cybersecurity is crucial. Regularly revisiting and updating security policies and procedures ensures that development teams are always adequately prepared to respond to new and complex threats. This unyielding commitment to security advancements allows organizations to remain ahead of adversaries and continuously safeguard their digital infrastructure. Ultimately, the cornerstone of any sound security strategy lies in adaptation and perseverance, ensuring long-term success in countering cyber threats. The journey to secure software development is ongoing, demanding diligence and a proactive approach to navigating risks and vulnerabilities effectively.
Pave the Path Forward
In recent years, the cybersecurity domain has grown more intricate and hazardous, presenting substantial threats to contemporary software development. High-profile cyberattacks have highlighted the vulnerabilities even in the most fortified applications, making security an indispensable element of a developer’s toolkit. The scale of threats businesses confront now emphasizes the urgent demand for secure coding techniques to ensure user protection and safeguard organizational resources. This article presents an all-encompassing strategy for embedding robust security measures throughout the software development lifecycle. Developers, by adopting these ten vital steps, can significantly bolster defenses against malicious threats, ensuring the protection of crucial data and intellectual assets. Emphasizing security in software creation not only helps in fortifying applications but also in establishing a resilient foundation that can withstand evolving cyber threats, thereby safeguarding user trust and business credibility for the future.